SAP Pentest
https://github.com/lazaars/SAP-Pentest
A quick methodology on testing/hacking SAP Applications for n00bz and bug bounty hunters
by: Jay Turla (@shipcod3)
A list of SAP NetWeaver default passwords
USERNAME PASSWORD
SAP* PASS
SAP* 06071992
DDIC 19920706
EARLYWATCH SUPPORT
TMSADM PASSWORD
TMSADM $1Pawd2&
SAPCPIC ADMIN
Discovery
Check the Application Scope or Program Brief for testing. Take note of the hostnames or system instances for connecting to SAP GUI.
Use OSINT (open source intelligence), Shodan and Google Dorks to check for files, subdomains, and juicy information if the application is Internet-facing or public:
inurl:50000/irj/portal
inurl:IciEventService/IciEventConf
inurl:/wsnavigator/jsps/test.jsp
inurl:/irj/go/km/docs/
https://www.shodan.io/search?query=sap+portal
https://www.shodan.io/search?query=SAP+Netweaver
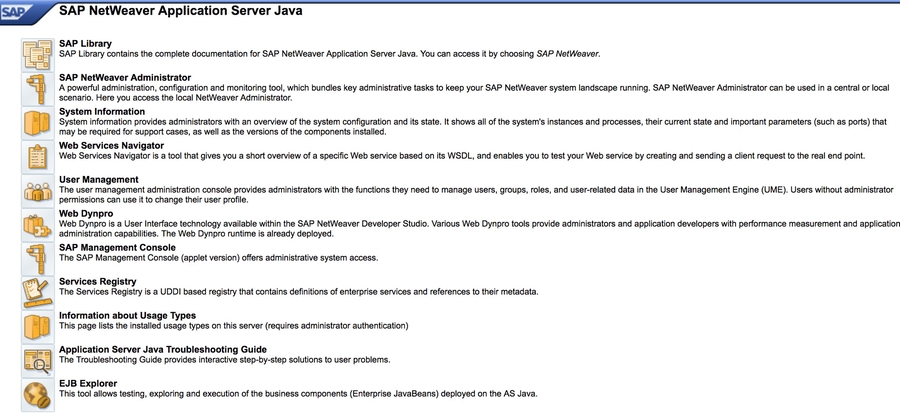
https://www.shodan.io/search?query=SAP+J2EE+EngineHere is what http://SAP:50000/irj/portal looks like
Use nmap to check for open ports and known services (sap routers, webdnypro, web services, web servers, etc.)
Crawl the URLs if there is a web server running.
Fuzz the directories (you can use Burp Intruder) if it has web servers on certain ports. Here are some good wordlists provided by the SecLists Project for finding default SAP ICM Paths and other interesting directories or files:
Run bizploit's discovery plugins (note: customized script from davehardy20):
Use the SAP SERVICE DISCOVERY auxiliary Metasploit module for enumerating SAP instances/services/components:
Document the findings.
Testing the Thick Client / SAP GUI
Here is the command to connect to SAP GUI
Check for default credentials (In Bugcrowd's Vulnerability Rating Taxonomy, this is considered as P1 -> Server Security Misconfiguration | Using Default Credentials | Production Server):
Run Wireshark then authenticate to the client (SAP GUI) using the credentials you got because some clients transmit credentials without SSL. There are two known plugins for Wireshark that can dissect the main headers used by the SAP DIAG protocol too: CoreLabs SAP dissection plug-in and SAP DIAG plugin by Positive Research Center.
Check for privilege escalations like using some SAP Transaction Codes (tcodes) for low-privilege users:
Check if you can execute system commands / run scripts in the client.
Check if you can do XSS on BAPI Explorer
Testing the web interface
Crawl the URLs (see discovery phase).
Fuzz the URLs like in the discovery phase. Here is what http://SAP:50000/index.html looks like:
Look for common web vulnerabilities (Refer to OWASP Top 10) because there are XSS, RCE, XXE, etc. vulnerabilities in some places.
Check out Jason Haddix's "The Bug Hunters Methodology" for testing web vulnerabilities.
Auth Bypass via verb Tampering? Maybe :)
Open
http://SAP:50000/webdynpro/resources/sap.com/XXX/JWFTestAddAssignees#then hit the "Choose" Button and then in the opened window press “Search”. You should be able to see a list of SAP users (Vulnerability Reference: ERPSCAN-16-010 )Are the credentials submitted over HTTP? If it is then it it is considered as P3 based on Bugcrowd's Vulnerability Rating Taxonomy: Broken Authentication and Session Management | Weak Login Function Over HTTP. Hint: Check out http://SAP:50000/startPage too or the logon portals :)
http://SAP/sap/public/info contains some juicy information:
Attack!
Check if it runs on old servers or technologies like Windows 2000.
Plan the possible exploits / attacks, there are a lot of Metasploit modules for SAP discovery (auxiliary modules) and exploits:
Try to use some known exploits (check out Exploit-DB) or attacks like the old but goodie "SAP ConfigServlet Remote Code Execution" in the SAP Portal:
Before running the
startcommand on the bizploit script at the Discovery phase, you can also add the following for performing vulnerability assessment:
Other Useful Tools for Testing
PowerSAP - Powershell tool to assess sap security
Burp Suite - a must have for directory fuzzing and web security assessments
pysap - Python library to craft SAP network protocol packets
References
https://github.com/davehardy20/SAP-Stuff - a script to semi-automate Bizploit
Last updated